Delete Kafka Data Without Deleting It: Crypto Shredding for GDPR Compliance
Kafka data deletion is slow and unreliable. Crypto shredding makes data unreadable instantly by destroying encryption keys.
Data privacy regulations require you to permanently erase personal data on request. Kafka's append-only log makes this nearly impossible through traditional deletion.
Crypto shredding solves this by making encrypted data instantly and permanently unreadable: destroy the encryption key, and the data becomes useless.
The Cost of Non-Compliance
GDPR Article 17 grants individuals the "right to be forgotten." Failure to comply costs up to €20 million or 4% of global annual revenue, whichever is higher.
CCPA violations carry penalties of $2,500 per unintentional violation and $7,500 per intentional violation, plus exposure to consumer lawsuits.
Without a reliable way to erase data from distributed systems like Kafka, you risk financial penalties, customer trust erosion, and operational drag.
Why Kafka Makes Traditional Deletion Impractical
When a customer requests data deletion, teams typically resort to manual processes, custom scripts, and ad-hoc tools. Each team approaches it differently, creating inconsistency, errors, and compliance gaps.
The core problems:
- Finding the data: Large datasets scattered across unknown replications and Kafka Connect pipelines
- Deleting the data: Slow, expensive, error-prone, with no guarantee of success. Kafka's append-only log makes physical deletion architecturally hostile.
- Proving compliance: Regulations require timely, verifiable deletion. Fragmented processes create audit nightmares.
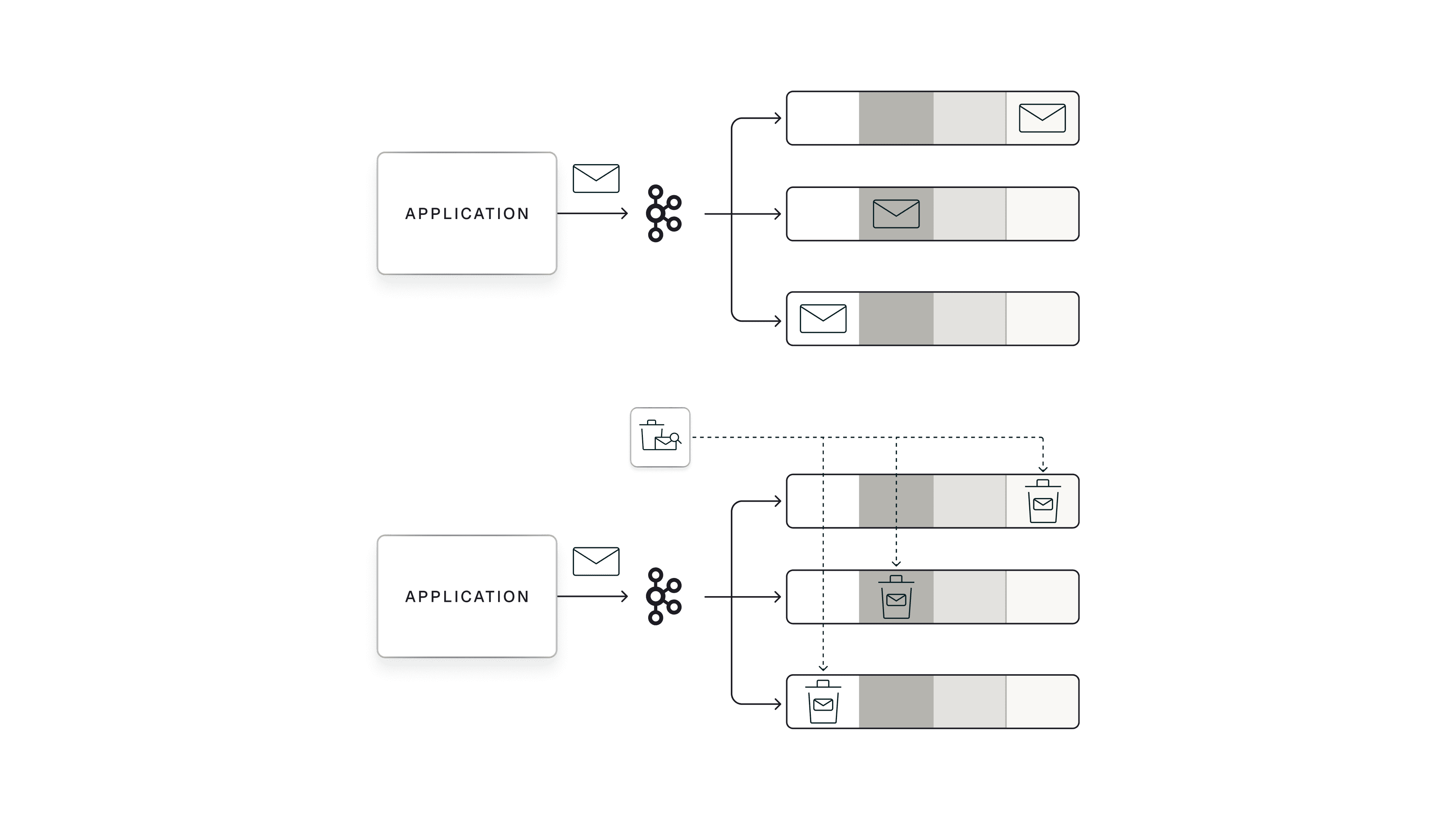
How Crypto Shredding Works
Crypto shredding makes encrypted data permanently inaccessible by deleting the encryption key. Instead of removing data from storage (slow and costly), you render it unreadable instantly across all systems by destroying a single key.
For Kafka, effective crypto shredding requires balancing security, cost, and operational simplicity.
The Cost Problem with Per-User Encryption Keys
Cloud-based key management systems (KMS) charge per key per month. Per-user encryption becomes prohibitively expensive at scale.
AWS KMS caps keys at 100,000 per account by default. Self-managed key storage introduces operational complexity, security risks, and maintenance burden that often matches or exceeds cloud KMS costs.
Architectural constraints compound these issues. You need scalable storage, low-latency access, and efficient key rotation without performance bottlenecks. Adding new infrastructure components creates friction with security and platform teams.
Without a well-designed solution, you face high costs, operational overhead, compliance failures, and potential data exposure.
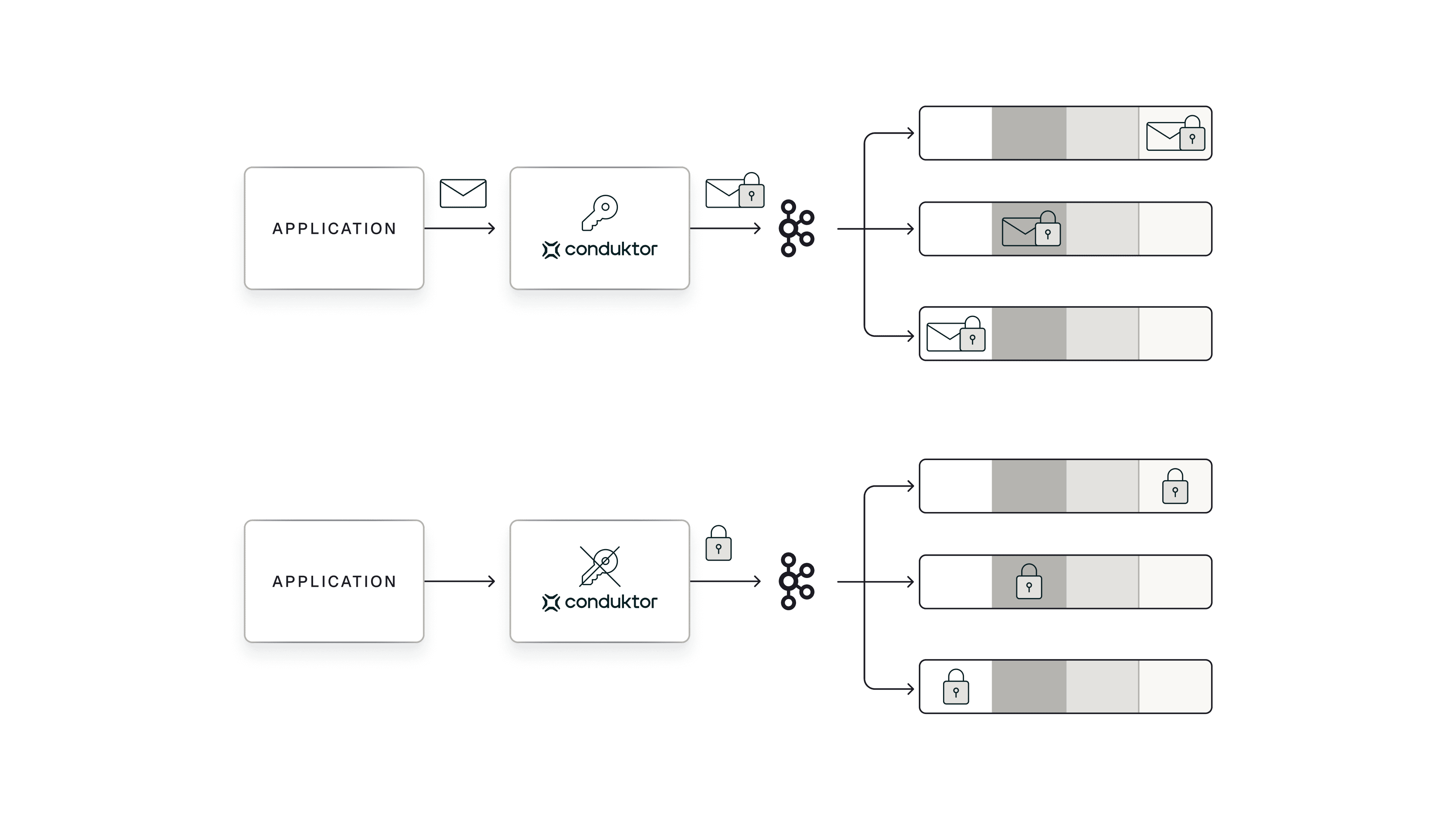
How Conduktor Implements Crypto Shredding
Conduktor provides a cost-efficient, scalable solution without expensive per-user cloud keys or complex self-managed vaults. Keys are derived from a central master key and stored securely in Kafka itself.
The flow:
- Every Kafka message flows through Conduktor
- A user-specific encryption key is generated from a central master key (provided by an external KMS like AWS KMS)
- This user-specific key is stored securely within Kafka
- All messages from one user are encrypted using their unique per-user key
- When a deletion request arrives, the key for that UserID is permanently removed
Deleting the key instantly makes all associated data unreadable.
Getting Started
Crypto shredding addresses compliance requirements without complexity or excessive cost. Conduktor makes it simple, scalable, and secure as part of Conduktor Shield.
Get in touch to see how it works.
